October 2019 | Point of View
Proactive, predictable, prioritized: An evolution in cyber risk planning
Proactive, prioritized, and purposeful planning is essential for an organization to become cyber resilient
- Proactive, prioritized, and purposeful planning is essential for an organization to become cyber resilient. We have distilled our lessons learned in the field into guidelines for what to do before, during, and after a cyberattack. In all three stages, there are crucial elements that, if implemented correctly, will ensure a posture of cyber resiliency.
- Adopting a cyber resiliency mindset will lead you to reconfigure teams, create new action plans, and implement regular system tests and drills.
- Get creative when thinking about where and how threats can be detected. Instead of relying on a daily report to assume you’re safe, consider other ways your systems are at risk. How are you thinking about browser anomalies? Risky downloads? Remote workers? Everything needs to be considered.
- Creating a resilient business model is a large undertaking, requiring ongoing commitment from every level of the enterprise. But done well, firms are left more robust and more valuable.
Introduction
In the world of cybersecurity threats, there are knowns and unknowns.
As organizations continue to adopt new technologies and digitize every aspect of their revenue generation, attackers are constantly evolving to strike where it may hurt an organization most. Where and when the next threat will strike, what form it will take, and which vulnerabilities will be exposed are all unknowns. What is known is that, eventually, all organizations will experience breaches and disruptions.
It may seem impossible to plan and prepare for a world of unknown threats, and that’s why at West Monroe, we’re changing the cybersecurity paradigm from trying to measure risk—which is an intangible—to evaluating the ability to withstand an attack, minimize operational disruption, and bounce back quickly: a holistic approach to cyber risk planning known as resilience. Rather than thinking about cybersecurity in narrow terms as a technology or IT issue, or simply a compliance exercise in protecting consumer data, our Cyber Resiliency Mandate is all about how to holistically implement process and procedures throughout the organization to limit the business impact of a security incident.
Proactive, prioritized, and purposeful planning is essential for an organization to become resilient. We have distilled our lessons learned in the field into guidelines for what to do before, during, and after a cyberattack. In all three stages, there are crucial elements that, if implemented correctly, will ensure a posture of cyber resiliency.
Chapter 1: Before a cyberattack
Instead of moving from crisis to crisis, responding in a reactionary manner, leadership teams must take a farsighted view and recognize the question of cybersecurity and resilience for what it is—a foremost priority for long-term investment. It’s as critical to a business’ long-term success as careful management of the company budget.
Perhaps most significantly, adopting a cyber resiliency mindset will lead you to reconfigure teams, create new action plans, and implement regular system tests and drills. In many ways cyber resiliency calls for complete culture change, which can be intimidating. But now is the time to start making the moves that will fully protect your business.
Rather than implementing point solutions to nebulously improve cybersecurity, make sure that the improvements being made to the environment increase your ability to defend against an attack or to respond and recover more quickly. For example, make sure disaster recovery and backups are segmented such that they would not fall victim to an attack, and would be available when they are needed most.
You’ll want to focus on and prioritize the following:
Develop and document a business continuity plan
As a best practice and staple of good governance, many firms engage in continuity planning when it comes to natural disasters or critical personnel. But this kind of thinking needs to spread to cybersecurity, which should be handled as a multi-faceted and company-wide effort with engaged leaders setting a plan to maintain the highest levels of operational continuity.
That plan should include not only how to get infrastructure back online but how to react if, for instance, employees must work from home. This plan should have a “business service” lens, addressing everything people need to keep doing their jobs and how to deliver those capabilities—be they digital tools, payroll, communication strategies, or otherwise—so they can continue working amid the disruption.
On this front, a detailed communications plan is critical. Think through assumptions like not having access to email, or not being able to look up digital contacts. You’ll need a plan to communicate internally and externally.
Identify the necessary external partners you’ll need to address the breach and expedite the recovery. Most likely that will include outside counsel, a cybersecurity insurance provider, a public relations or crisis management team, preferred external technical vendors, as well as back up options for each of these critical areas.
Lastly, be sure to regularly test and update the business continuity and incident response plans. Make sure that the plan captures new or changed business processes and applications, that everyone in the organization understands their roles, and that everyone has a backup. Ransomware doesn’t wait for people to come back from vacation, so identifying key personnel risks and gaps in the plan can keep teams from fumbling when it comes time to use the plan for real.
Define common risk areas and prioritize appropriately
Identify key leaders, resources, and dependencies— and assemble your all-star resiliency team. Consider who would be the most vocal and crucial in the event of loss of revenue-generating activities. Pulling these key stakeholders from IT, business, sales, executive committees, and external consultancies together for working sessions in a proactive manner will considerably decrease confusion and chaos during an investigation.
Through regular, high-priority planning sessions, the areas and dependencies most vulnerable to disruption from cyber threat will emerge. Identifying vulnerable risk areas will aid in efforts to create strategic redundancies and backups.
Create offline backups to make sure you can recover data
In the event of a network outage or compromised system, the critical data necessary for day-to-day business operations will likely be inaccessible. Therefore, ensuring proper offline backups of operationally critical data is paramount.
The key here is not to back up this data just anywhere on your network. The data must be stored offline or in a location where it can’t be encrypted, deleted, or otherwise compromised by an attacker. ”
This data capture should include images of servers being backed up, as well as backups of template images used to build servers and workstations. The former will allow for a faster recovery of those systems, while the latter will accelerate the rebuild process for those that need it.
The key here is not to back up this data just anywhere on your network. The data must be stored offline or in a location where it can’t be encrypted, deleted, or otherwise compromised by an attacker.
Consider what kind of dependencies and interactions rely upon different data streams—this is where your cross- sectional team proves its value: Folks from manufacturing or customer service might have a different line of insight into critical data systems and can flag issues that might be missed from the view of the IT department alone.
Establish monitoring protocols to enhance detection capabilities
To achieve full cyber resiliency, it’s not enough to simply set a firewall or antivirus software on auto pilot.
We’ve seen many cases where system-wide firewalls did not prevent malware from infecting individual workstations and, in doing so, allowed the potential compromise of the whole network.
Consider investing in tools to analyze network activity on an individual server- and workstation-level. It’s not uncommon to see attackers dwelling in a client environment for six months or even longer before a client experiences the impact of a ransomware attack. Given such time horizons, analyzing granular data in real-time can help catch these problems when they’re small and prevent them from growing into something more impactful to the business.
Improve authentication and authorization—even if it takes extra steps
Resilience is about redundancy and protection, often at the cost of convenience. It may be inconvenient for employees to log in with multi-factor authentication but doing so reduces the severity of credential compromise due to phishing emails for the entire enterprise. Utilizing the best practices of organizational change management, leadership must take seriously the need to educate and guide employees in understanding the risk of unsafe individual practices and modeling expected changes.
If you haven’t examined your Privileged Access Management protocol in a while, it’s time you took another look. This is another area we see lax security in the name of convenience. Do you have adequate control of permissions and a process for business requirement driven privileged access management? Users who have administrative accounts should separate their privileged accounts and only use them for functions that require them (e.g., development, testing, administration).
These accounts should be secured with multi-factor authentication and not used for day-to-day activities such as email or integration with any third-party applications to limit the likelihood of compromise of the highly sensitive credentials.
Hypothesizing a plan is not enough, it needs to be stress-tested with technical recovery tests and table- top exercises
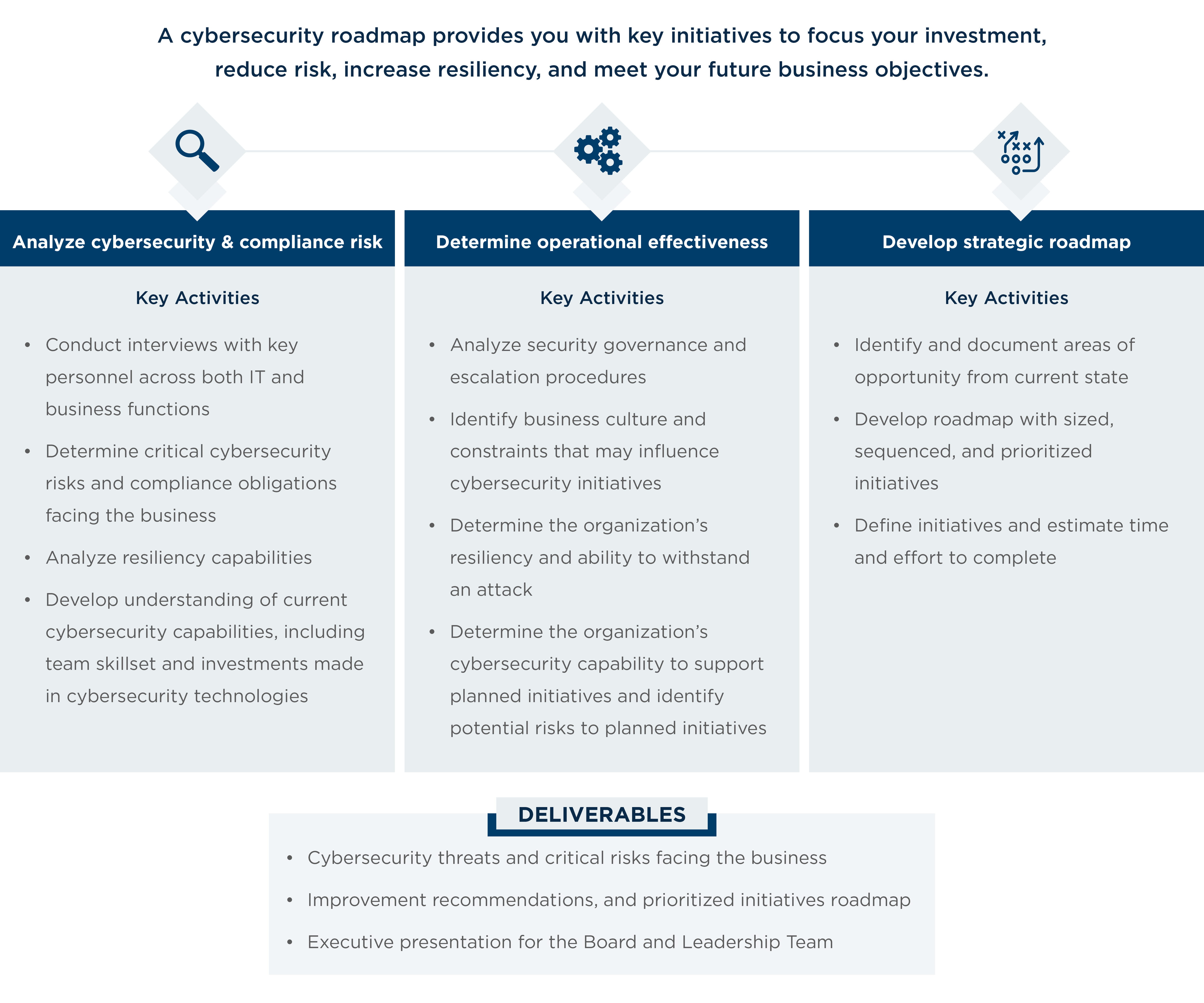
Documented and publicized technical recovery and business continuity plans should be treated as living and breathing documents that need to be adapted, revised, and stress-tested to be proven effective. Too often we see organizations task siloed IT admins, who may not have a day-to-day engrossment in business operations, with developing these plans. Without peer review and gap identification, these plans will quickly grow stale and ineffective during a response.
Utilizing the best practices of organizational change management, leadership must take seriously the need to educate and guide employees in understanding the risk of unsafe individual practices and modeling expected changes. ”
Conclusion
Just by getting started on these initiatives, organizations can shift the mindset toward a more proactive approach to security. This shift can help engage key resources, form a team dedicated to these issues, and improve cyber resiliency in years to come.
In the event of a probable cyberattack, like any natural disaster, the shortest path to restoring normal business operations is to have already embraced the resiliency mandate: Establish the response plan, drill and test the plan, and hone your ability to respond to crisis with practiced muscle memory.
Chapter 2: During a cyberattack
As with planning ahead to mitigate the business impact of a cyberattack, there are clear dos and don’ts for organizations to keep in mind while undergoing a breach in real time.
Most incident response is a hyper-focused technical effort set on identifying the source and party responsible for the attack—which does little to help orient technical (and non-technical) efforts toward business continuity and returning to revenue generating operations as quickly as possible.
Preparing to take the right steps to target issues, properly document incidents, and communicate (potentially without a functioning network) effectively to key leaders is critical in minimizing downtime.
Here are some ideas to ensure your organization responds effectively in the midst of a cyberattack:
Know what to preserve for evidence— and how to preserve it
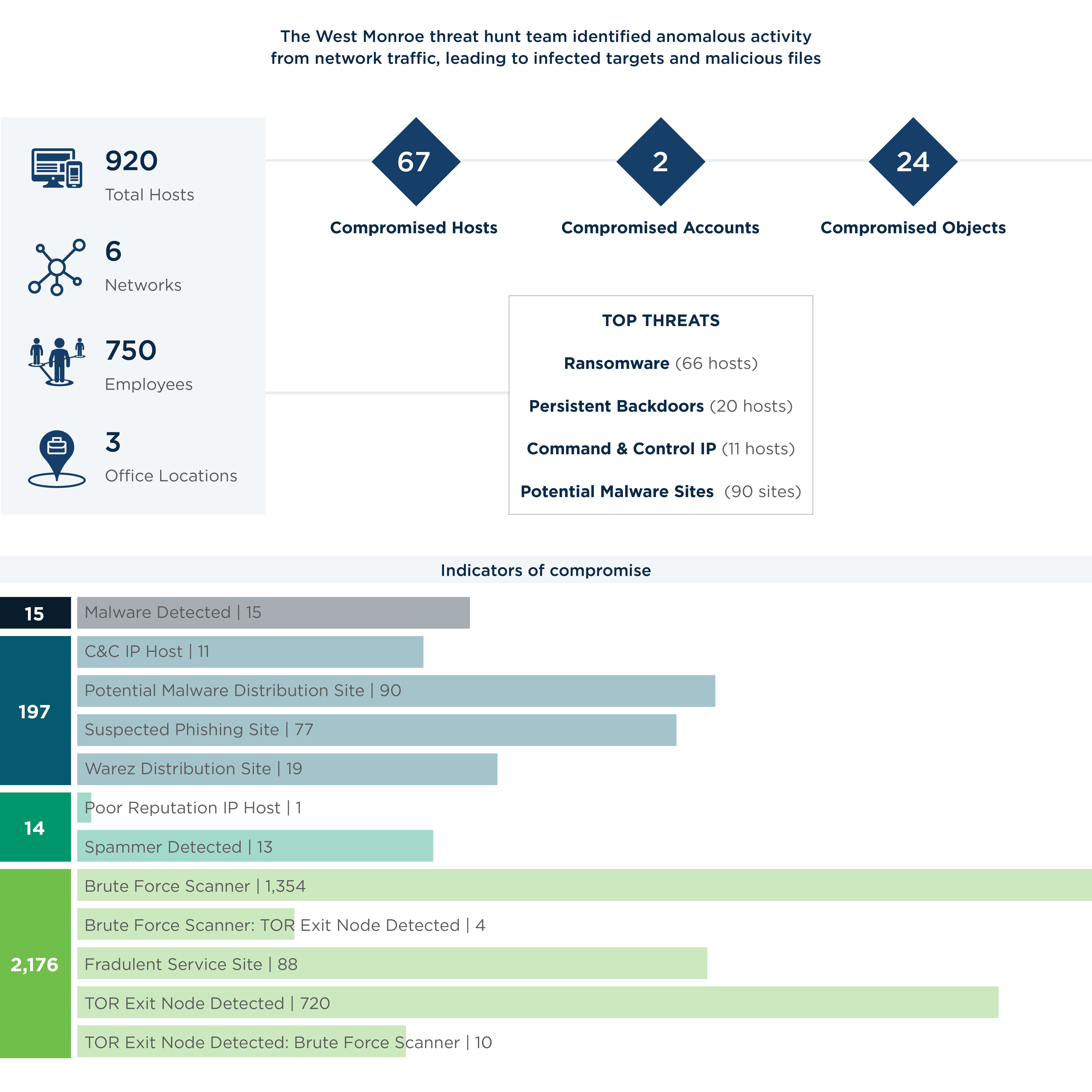
The goal of a forensic investigation during an incident should focus on uncovering the lapse in security that allowed the attacker in, what remediation steps can mitigate the attackers’ foothold, and how to identify possible pivot points for other attacks in the environment.
Along the way, you’ll need to know how to prioritize evidence collection and preservation and how to secure the evidence required to accomplish the investigation task without inhibiting recovery efforts. Too often, we see companies relying on full forensic image captures as the only source of investigation, which can be a logistical nightmare. Although at times necessary, it has been our experience that most information required for incident triage is found in Windows Event logs that could be quickly harvested en masse.
We often see companies fall into a common trap, going down a rabbit hole of spending too much precious time and resources trying to figure out the identities of the attackers. In the moment, the “who?” question is not as important as the “how?” Prioritize information gathering that reveals how the attack occurred so that you can stop it in its tracks and protect your network against future incidents.
Threat-hunt, outside the box
To return to normal operations as quickly as possible, many companies will acutely focus on the specific workstations or servers that appear to be compromised.
But this approach misses the forest for the trees. System vulnerabilities likely extend beyond obviously infected machines or servers. For example, the vulnerability that allowed Server #1 to become infected, might also be present in Servers #2–#10. Leaving these other systems unaddressed could allow for attackers to come back in and continue compromising your network systems.
A full-blown ransomware attack, for example, is usually the last stage of a cyberattack. You can’t assume that the systems with ransomware on them were the only ones compromised; there could have been numerous other malware droppers used before the attack culminated in a ransomware release.
Get creative when thinking about where and how threats can be detected. That’s where proactive hunting comes into play. Instead of relying on a daily log report to assume you’re safe, consider other ways your systems are at risk. How are you thinking about browser anomalies? Risky downloads? Remote workers? Everything needs to be considered.
Activate the incident command team
In the planning before an attack, an organization should have identified a first-in-line incident response team; a team prepared to quickly mobilize, put the incident recovery plan into play, and guide the organization’s return to normal operations as quickly as possible.
During an attack, this team will be armed to make decisions and communicate priorities to management and employees. There will be a lot of questions and chaos in the thick of an incident, and the incident command team’s job is to have the answers, thereby mitigating the chaos and streamlining response efforts. This includes working with both internal and external resources to set priorities for triage, forensic investigation, business resumption, knowledge distribution, and executive reporting.
As you may imagine, or may even know firsthand, an incident response situation is extremely stressful for all parties. There are questioning executives, frantic administrators, furious business partners, and confused end users, having a key resource that is organized, calm, and collected in the middle of it all will aid in delivering an effective and efficient incident investigation.
There will be a lot of questions and chaos in the thick of an incident, and the incident command team’s job is to have the answers, thereby mitigating the chaos and streamlining response efforts. ”
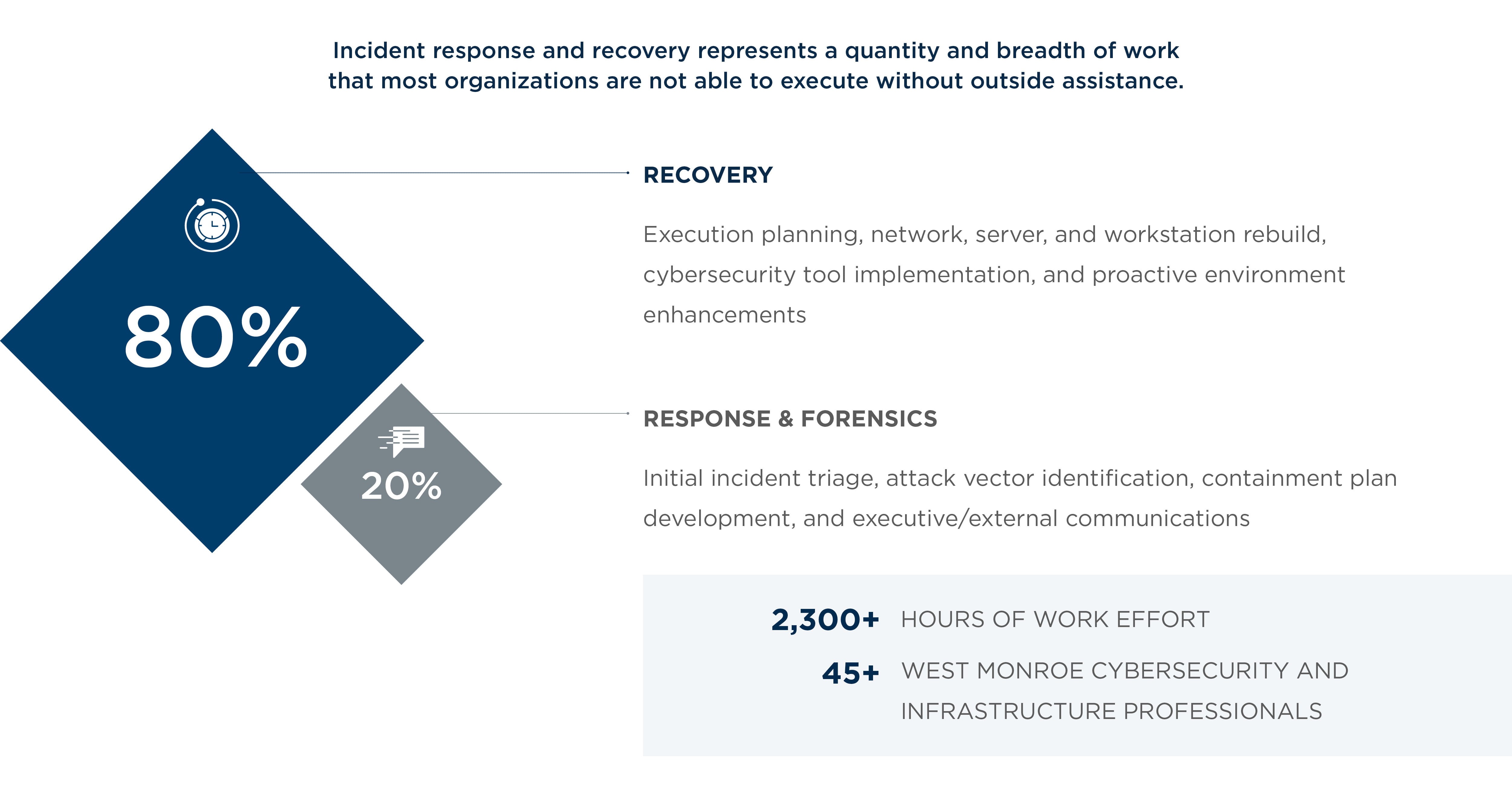
Prioritize remediation of critical systems and functions—to get your business up and running
Doing so requires taking inventory of not just infected/ encrypted systems, but the entire infrastructure.
We worked with a financial services company to aide in its recovery after an incident.
- Segmenting network services to create a clean network and isolate potentially infected machines
- Restoring basic infrastructure services, such as authentication, through Active Directory
- Deploying tools to recover deleted backup data
- Considering approaches for recovering over 700 workstations that could no longer be trusted as unaffected by the attack.
As you go, know that different systems may require different forms of forensic data collection and different recovery methods. Knowing when to grab logs and when to grab images, then, is key here.
Conclusion
For organizations experiencing the chaos and calamity of a security incident, effective planning and efficient procedures for how to respond in the heat of the moment is essential for resuming revenue-generating capabilities.
Balancing the near-term objective of shutting the threat down with longer-term concerns of identifying remaining vulnerabilities and properly collecting evidence can be tricky. But it’s possible with clearly delineated teams, priorities, and action plans.
Chapter 3: After a cyberattack
After experiencing a cyberattack, organizations typically initiate an investigation to determine the specific causes and resulting damage of the attack. Usually performed by external, professional Incident Response teams, these efforts include collecting technical forensics, identifying the root source of the attack, and determining the extent to which data and machines were compromised.
These activities are important and necessary. But if the investigation’s scope is limited too narrowly on technology, important aspects of ensuring future business continuity will be left unaddressed. In the aftermath of incident recovery, be careful to address the full scope of the damage caused, identify and resolve gaps and ensure upgraded resiliency measures. Assessing not only the acute damage done from the incident, but also your level of preparation before the attack, and how you executed recovery measures during the attack are important aspects of ensuring continued resiliency.
See the attack through a business-oriented lens
Consider that when cybercriminals breach critical systems, the risk to your business goes far beyond compromised data and compliance. When a cyberattack happens, being caught flat-footed and unable to react means prolonging a period of operational shutdown, lost revenue, unforeseen legal and technical costs, communication chaos, and most crucially, canceled services and missed expectations for customers.
As things settle down in the aftermath of an attack, ask yourself: did my organization have the right recovery goals from a business continuity perspective? Was there a list of the most critical tasks to accomplish to limit downtime? Did we understand what key systems were more important to restore in order to operate the business? This is the best time to revisit existing incident response, disaster recovery, and business continuity plans to ensure that they are accurate based on the work that’s just been performed to recover.
Remember to think specifically about the impact to customers in both a total shutdown and slower recovery scenarios. How can you continue to provide services to customers? How can you minimize trust loss? What will you tell them? Organizations would do well to plan ahead for the days immediately following an attack and staff up both their company’s internal IT help desk as well as customer facing support infrastructure. Internal employees dealing with the inconvenience of an attack and customers facing service disruption will drive an increased number of incoming support calls. Additionally, responders should be prepared to escalate any particularly concerning items to the recovery team, while having a consistent message to give to both internal and external audiences that can answer questions without spreading or prompting rumors.
Upgrade systems and increase hardening and security standards
While helping a client navigate the recovery process after a security event, we faced an immediate challenge: namely, that the organization’s workstation environment included a mix of Windows 7, 8, and 10, with three different versions of Microsoft Office. Over the next eight hours, our team had to devise a plan to rebuild and standardize the platform on Windows 10 and Microsoft Office 365 with enhanced security configurations.
This was a challenge during the fast-paced recovery efforts, but ended up being a blessing in disguise— when else do you have the opportunity to upgrade all workstations and end-user devices in one pass? These sorts of upgrades can also simplify administration and management burden by standardizing previously dissimilar configurations, resulting in time savings for IT support teams.
Remember to think specifically about the impact to customers in both a total shutdown and slower recovery scenarios. How can you continue to provide services to customers? How can you minimize trust loss? What will you tell them? ”
After the initial rush to restore business operations, organizations can use this opportunity to do away with insecure business norms, by implementing multi-factor authentication or hardening processes for credential sharing. These changes often come with a level of business disruption that is more palatable or more easily justified in the aftermath of an attack, so don’t miss the chance to get a more disruptive project approved and executed.
It’s also important to think long term and focus on investment and planning that can limit the impact of future attacks. Key projects include implementing multi-factor authentication for remote access, deploying privileged account management for domain administer administrator accounts, and segmenting the network to limit traversal and support modular survivability.
Conclusion
After an organization experiences a cyberattack there can be a lot of confusion, chaos, and competing priorities. As important as the technical forensic investigation is to discover the details of the nature of the attack, what was affected, and how the attacker penetrated systems, it is also critical to ensure you are examining all aspects of the business and how you can improve your posture and ability to respond to a future incident.
Ultimately the goal of follow-on projects and planning is to minimize service disruption and loss of trust with your customers—while ensuring that you are adequately protected to withstand and recover in the event of a future attack. It all comes back to thorough and consistent planning.
A commitment to creating a resilient business model is a necessity. It is not as simple as running a penetration test or buying and installing a state-of-the-art firewall. These are absolutely great things to do from a cybersecurity standpoint, but an organization needs a blend of process and technology: from well-documented and tested business continuity, disaster recovery, and incident recovery plans, to hardened networks and systems, enhanced credential segmentation and authentication mechanisms, and modern security tools. Crucially, both the processes and tools must be revisited regularly, and updated as the threat landscape changes.
Creating a resilient business model is a large undertaking, requiring ongoing commitment from every level of the enterprise. But done well, there’s no doubt firms are left more robust and more valuable.
In this whitepaper we highlighted some of the key lessons from our cyber practice to help you get started. At West Monroe, our deep bench of experts are deployed in the field to help our clients achieve their resiliency goals. Ready to learn more about what upgraded cyber resiliency would look like at your organization? Contact us to find out how we can help make your organization stronger, more secure, and fully resilient.